Foundations in Finance
Since the early 2020s, the pandemic, greater digitalisation and heightened geopolitical tensions have raised the risk of cyber-attacks. The International Monetary Fund (IMF) reports that attacks on financial firms account for nearly one-fifth of all cyber-attacks. Financial organisations are more exposed, representing a viable target for various Threat Groups with a range of motivations. Firms can manage systemically important assets, store and process large amounts of sensitive data or offer a vehicle for monetary gain through compromise of payment systems.

More recent developments add fuel to the fire, and would it be a blog post in 2024 without an AI reference? The UK’s public Cyber-Security arm, NCSC, states that AI will almost certainly increase the volume and impact of cyber-attacks in the next two years. In the face of mounting threats, Regulators view intelligence-led frameworks as a vital tool in understanding resilience across industry. Intelligence-led frameworks provide firms with a structured approach to understanding threat actors and cybersecurity threats through realistic, scenario-based testing. Before we unravel the growing landscape of frameworks, it is useful to touch on other key factors driving their adoption.
Cyber: tunnel-visioned terminology traps
Cyber itself is defined as_: cy·ber ˈsī-bər. : of, relating to, or involving computers or computer networks._ But it is much more. When an organisation wants to strengthen Cyber resilience, they tend to focus on ‘shiny boxes’. What about the supporting people and processes? Significant investments in technologies may have been made, with impressive supporting statements such as “AI-powered Heuristic Anomaly Detection”. The stark reality is that successful inclusion of technology in a defensive capability is reliant on the following:
- The support of a skilled and capable team.
- The continuous assurance of its effectiveness.
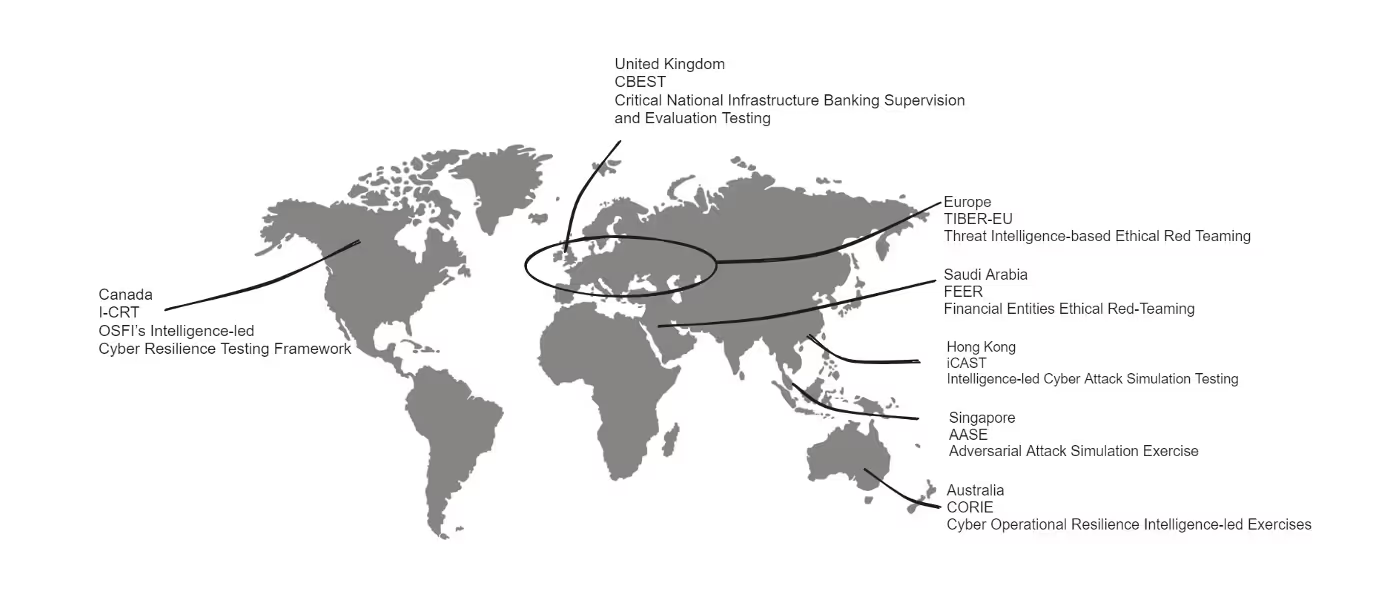
Testing of Cyber resilience across people and process is still immature outside of intelligence-led activities, with organisations resorting to vulnerability scans and configuration-led penetration tests to support resilience claims. Compliance activities can also result in organisations being guilty of using accreditation as a badge of Cyber resilience. Regulators see firms falling into these traps alongside the associated false sense of capability it gives them. By 2025, it is estimated that cybercrime will cost $10.5 trillion globally, increasing by 15 percent year on year. Against this backdrop, we are witnessing regulatory authorities and industry bodies across the globe starting to act, with many creating their own intelligence-led frameworks to bolster cyber resilience across their jurisdiction. This represents a form of regulatory intervention, as tolerance levels decline for organisations who are not addressing cyber resilience effectively. A quick look at several regulatory testing frameworks across the globe presents a daunting picture, but an initial focus on three frameworks – CBEST (UK), TIBER-EU (Europe) and iCAST (Hong Kong) highlights consistent similarities and expectations.
CBEST (Bank of England’s Framework)
The Bank of England describes CBEST as a targeted assessment that allows regulators and firms to better understand weaknesses and vulnerabilities and take remedial actions, thereby improving the resilience of systemically important systems. Despite not being mandatory, the regulatory bodies (FCA and PRA) strongly recommend regular CBEST exercises and there can be enhanced supervision if a firm is found to have significant vulnerabilities. The regulator may advise and support remediation actions to drive improvements.
CBEST & Friends
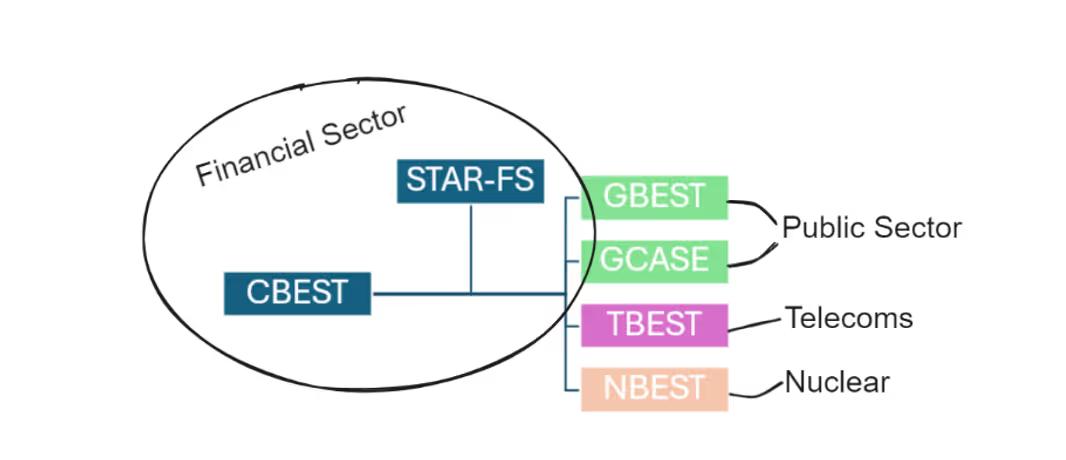
As something of a ‘Founding Father’, CBEST has been emulated by other frameworks. A notable example is GBEST – where:
- Regulator -> Government Advisory Function (the Cabinet Office)
- Financial firm -> Public Sector body offering key services to the population (in some cases managing critical national infrastructure)
Like CBEST, the framework seeks to build cyber resilience, but in a different sector. The same certifications are required of third parties, who utilise an identical testing methodology. Regarding the term ‘Founding Father’, does the lack of a United States-based framework in the map above suggest that intelligence-led Testing in the US is the ‘wild-west’? The truth is, ‘kind of’. A framework at Federal level does not appear to exist, although Departments like CISA are known to run ‘SilentShield’ assessments which incorporate key elements of the intelligence-led frameworks discussed - confirming that capabilities in the US exist (limited to a select few). With the recent finalisation of the SEC rules on cybersecurity disclosures, it is hoped that a formal, regulatory-led framework will emerge, formalising cyber resilience across the US market.
TIBER-EU
Initially developed as TIBER-NL in 2016 by De Nederlandsche Bank (DNB), it was later adopted by the European Central Bank (ECB), as guiding framework for EU financial institutions and re-badged ‘TIBER-EU’. Like CBEST it aims to enhance cyber resilience, but across a wider region. It recommends threat intelligence-based ethical red-teaming, with controlled cyber-attacks that simulate real-life tactics and techniques utilised by real-world threat actors. A key differentiator from other regulatory-led testing is that TIBER-EU does not stipulate that the Threat Intelligence and Red Team phases of TIBER-EU are carried out by certified external third parties.
iCAST
Implemented by the Hong Kong Monetary Authority (HKMA) and aimed at firms within the region, iCAST evaluates an organisation’s ability to respond to realistic cyber-attack scenarios, with the goal of enhancing cyber resilience and detect/respond capabilities. During iCAST assessments, regulatory involvement is less ‘heavy-handed’ in comparison to a CBEST or TIBER-EU (where they provide frequent oversight). In some cases, iCAST testing does not enforce a Threat Intelligence phase of delivery, although the Red Team engagement must be conducted by a certified external third party.
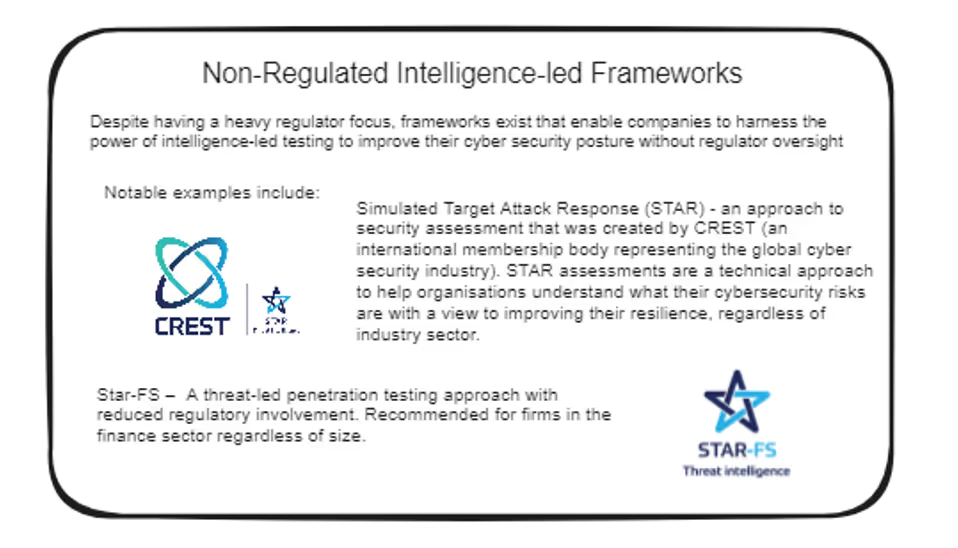
A Common Goal
Cyber Resilience is a term repeated across all frameworks and forms the common goal: “To strengthen Cyber Resilience by improving an organisation’s ability to identify threats, protect assets and detect, respond and recover from an attack.” A table unravelling the key properties of intelligence-led frameworks across the Financial Sector:
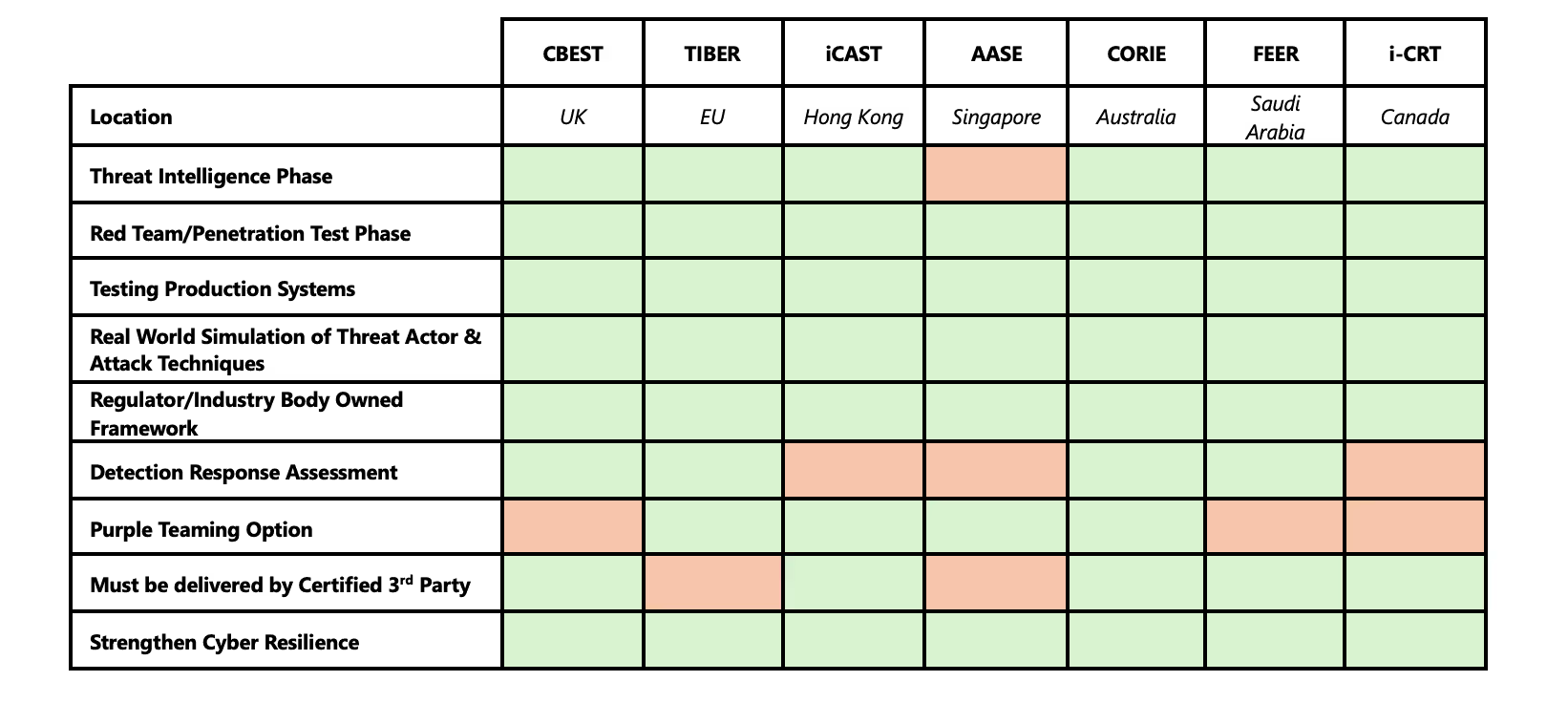
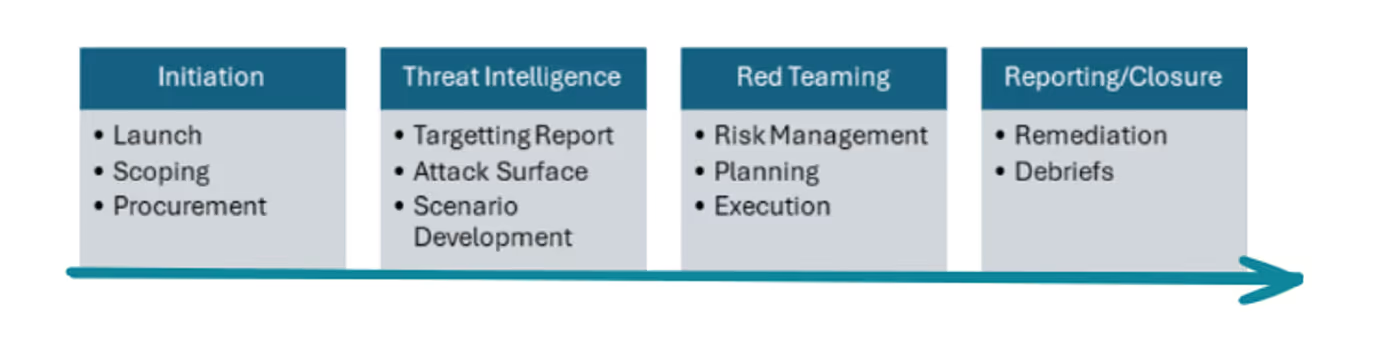
A prime differentiator is geography and the regulatory oversight/involvement. Where a firm operates, dictates the framework in use. In many cases, multi-national firms will look to perform cross-jurisdictional testing. Fortunately, there are common threads running through almost every framework that make this less of an issue. When conducting a test across multiple locations, firms must take the deepest elements of each to satisfy requirements. Intelligence-Driven: Most frameworks rely on Threat Intelligence. In doing so, they leverage real-world threat data to support the Red Teaming stages, ensuring realistic attack scenarios are delivered, where credible threats to the organisation are simulated. In some instances, for example TIBER-EU, there is a Generic Threat Landscape (GTL) Report which encompasses threats to that sector and geography, with the TI provider enriching it to form relevant scenarios that contextualise the firm's digital footprint and assets. Scenario-Based: Scenario-based testing is another commonality, often covering various attack types, such as phishing, external perimeter breaches, cloud credential theft, supply-chain and insider threat. This helps form the story of the attack, guiding the Red Team through relevant paths with the goal of impacting the confidentiality, integrity and/or availability of target systems. Testing is always carried out in production environments, exercising authentic detection which provides an insight into mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR). Risk Assessment and Resilience Enhancement: The frameworks aim to assess an organisation’s cyber resilience, by identifying vulnerabilities and weaknesses with corresponding remediation advice that they can understand and act upon, enabling structured and effective remediation. Typical Phases:
Conclusion Harnessing Threat Intelligence, frameworks enable a simulation of prioritised real-world threats. This measures the effectiveness of an organisation’s defensive capabilities, including people, process and technology to highlight and mitigate systemic business risks. As the number of intelligence-led frameworks grow and develop with authorities across the world recognising their value, it is easy to get bogged down in the prospective plethora of new acronyms. It is important to remember all frameworks share a common goal – to improve cyber resilience in the face of an evolving threat landscape and an ever-changing digitalised world. About the Author:
Bobby Spooner, a Principal Consultant at LRQA, specializes in managing risk for regulated testing across multiple geographies, utilizing intelligence-led frameworks. He holds the CREST Certified Simulated Attack Manager alongside CISSP and CCSP certifications and has extensive experience, including building and managing the Operational Security Assurance function for a major UK government department. As the designated Covid-19 Information Security Lead, he also handled urgent risk assessments to ensure secure operations in the post-pandemic environment. Additionally, Bobby has overseen Red and Purple Teaming engagements across the UK's Critical National Infrastructure (CNI), managing remediation projects to enhance security.